Access roles and permissions
Introduction
Access roles and permissions are used to restrict user access within Akkuro:
- Permissions restrict access to a certain action. For example, the ability to create a person is restricted by the permission "Create person", and updating a person is restricted by the permission "Update person".
- Access roles are a bundle of one or more permissions. For example, the role "Employee" has both the permissions "Create person" and "Update person".
Permissions follow the Create, Read, Update and Delete model and are defined for items on an attribute. An attribute for instance is "Person", while an item is "Document".
The access roles and permissions are defined in the configuration item. A configuration item needs to be applied to an environment as part of the configuration set.
Access roles
To create a new set of access roles and permissions, you can navigate to the configuration items using the action menu in the top right corner of the Configuration Portal, clicking on ‘Configuration Items’, then clicking ‘New’ > ‘Access roles and permissions’.
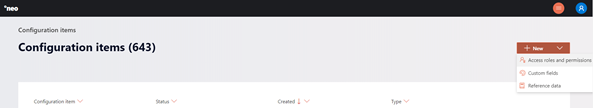
From here, you will start by configuring the access roles.
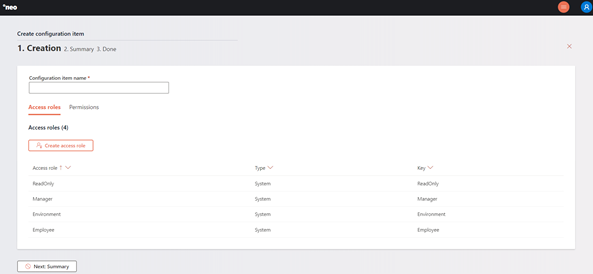
Each access role has the following characteristics:
Type
There are two types of roles, custom and system.
System roles
System roles are the roles that come standard with Akkuro. These roles have predefined names, keys and permissions. These roles are maintained by Akkuro and cannot be changed and/or deleted by you. The following system roles are available:
| Name | Key | Description |
|---|---|---|
| Employee | Employee | Provides user all permissions |
| Environment | Environment | Provides user access to environment. |
| Manager | Manager | Provides user all permissions. |
| Read only | ReadOnly | Provides user read only permissions. |
Custom roles
As a user, you can create roles of the type custom. These roles can be configured according to your specifications and can be updated and deleted at any time.
Name
The name of the access roles.
Key
A unique key (across all access roles and permissions configuration items) is required for each access role. Once the configuration item is completed, the key cannot be changed anymore.
Permissions
Permissions follow the standard Create, Read, Update and Delete processes as with all other configuration items, and are defined for items on an attribute.
Permissions are configured on the second tab of the Access Roles and Permissions wizard.
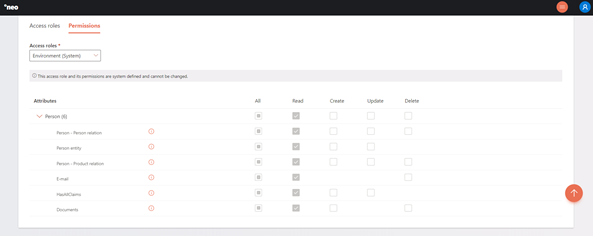
Available attributes are for instance Person and Loan. Items are defined per attribute and for instance are Person entity, document and e-mail for persons, and Loan entity and disburse for loans. Per item, the permissions can be indicated. However, it is possible that a permission is not applicable for an item.
The read permissions currently is always applied for each item and cannot be changed.
Updated 10 days ago